PureCrypter Deploys Agent Tesla and New TorNet Backdoor in Ongoing Cyberattacks
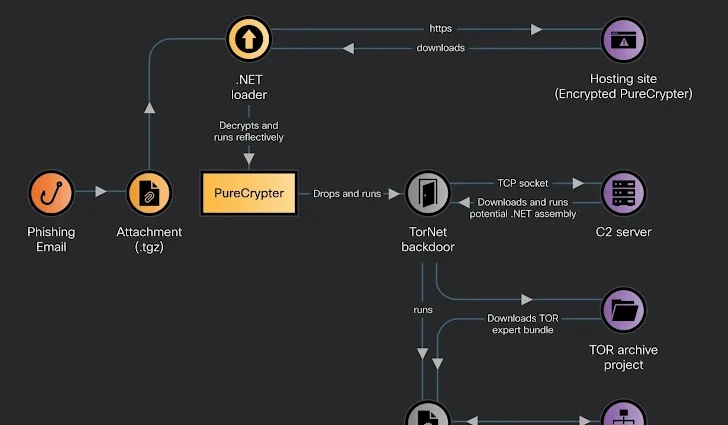
A new wave of cyberattacks has emerged, driven by the notorious malware distributor PureCrypter, which is using a combination of Agent Tesla and the newly discovered TorNet backdoor to target organizations and individuals. This ongoing campaign is a clear indication of the increasing sophistication of cybercriminals and their ability to evolve their tactics to remain undetected.
Agent Tesla, a widely known and highly effective information-stealing malware, has been a tool of choice for cybercriminals for years. It is capable of exfiltrating sensitive data, such as login credentials, email communications, and other personal or financial information. Agent Tesla uses advanced evasion techniques to bypass antivirus software and is often distributed through phishing emails or malicious attachments.
However, this latest attack introduces a new element: the TorNet backdoor. This custom malware, leveraging the Tor network, allows attackers to establish a persistent, anonymous communication channel with compromised systems. Once installed, TorNet grants cybercriminals remote access to infected devices, enabling them to execute commands, steal additional data, or install further malicious payloads. Its reliance on Tor makes it particularly difficult to trace, adding a layer of anonymity that complicates response efforts for security teams.
The ongoing PureCrypter campaign highlights the growing threat posed by multi-layered attacks, where attackers combine multiple types of malware to maximize damage and persistence. This shift to more sophisticated, hard-to-detect methods signals a rising challenge for cybersecurity professionals tasked with protecting organizations and users from advanced threats.
Experts urge businesses and individuals to remain vigilant and implement strong cybersecurity practices, such as avoiding unsolicited email attachments and ensuring robust endpoint protection. Regular updates to software and systems, along with user training on phishing attacks, can significantly reduce the likelihood of falling victim to such complex cyberattacks.